Identity has been a vital element right from the beginning in the human era. But in today’s fast pace world, especially when Technology is taking over almost all human tasks. Identity plays an important role, but even more important is to manage that identity.
Now a day, People are using so many applications and systems, which makes management of credentials a cumbersome task for end users. Let’s take an example, you have to remember so many credentials like Social Networking (Facebook, LinkedIn, Google+ etc.), Corporate (Office computer login, outlook, Skype, Business Applications etc.), Personal Financial (Internet Banking, Investments, Insurance Policies, etc.) and many more.
Your Enterprises can help you to minimize the number of credentials to remember, all it should do is to implement an appropriate Identity Management System and appropriate Single Sign-on solution. Below is the rough picturization of Identity management system, it may not be completely appropriate for every Enterprise, but with minor changes it should fulfill the Enterprise’s identity management requirement. Below example use few of the tools available in Market to depicts the working of building block in the framework.
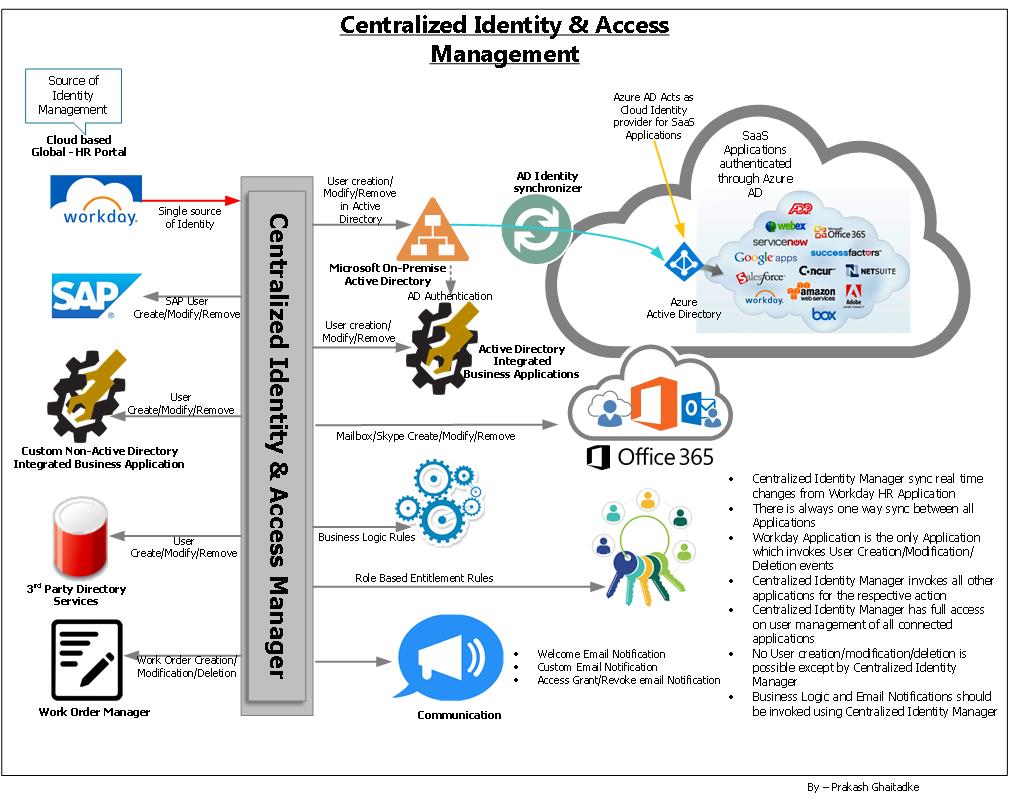
Workday: Is an on-demand cloud based financial management and human capital management software. HR Application is the book of truth for every Enterprise’s human resource management. So, more accurate the HR application data, the more streamline your Identity management system. Whenever a new user is on-boarded in HR Portal, it should generate an event and invoke Identity management system to create new user in its own database and other respective necessary applications.
Microsoft On-Premise Active Directory: As we all know Microsoft On-Premise Active Directory has been one of the most popular and widely used directory service available in the market and has been leading the market for more than a decade. Thus, Microsoft On-premise Active Directory is one of the most important Application in almost every Enterprise. Therefore, User ID creation in Active Directory becomes very vital.
Azure AD Connect (DirSync): Is Identity synchronizer between Microsoft On-Premise Active Directory and Azure Active Directory. It is very important especially when you have Hybrid environment. It syncs all the pre-defined or all supported objects to Azure Active Directory.
Azure Active Directory: is the SaaS (Software as a Service) Microsoft Identity Manager, it supports more than thousands of SaaS applications and the number is increasing day by day.
SaaS (Software as a Service) Applications: SaaS applications are fully cloud supported applications and sometimes most affordable applications to use. There are few Cloud Identity Management Providers in the market and Microsoft’s Azure Active Directory is one of them. Which provides Single Sign-on or like experience to most of the SaaS applications, even if the application is not listed, you can mark an email to Microsoft asking to provide Single Sign-On or like experience and your request will be taken care in next few hours if feasible. So, your corporate identity and credentials are still valid using Azure Active Directory over the Cloud, few examples are like, MS Office 365, Salesforce and so on.
SAP: In most cases SAP applications are not integrated with Active Directory but creating accounts in SAP application becomes an overhead, apart from that maintaining same naming conventions and passwords are also a hefty task, but with the help of Centralized Identity Manager it happens in the minutes keeping the standards as defined.
Custom Non-Active Directory Integrated Business Applications: There are many applications in every Enterprise which doesn’t support Active Directory in terms of sharing credentials or authentication, for such applications Centralized Identity Manager can help you to create User accounts and maintain it.
3rd Party Directory Services: There is still need of maintaining 3rd party Directory services in few Enterprises for some or the other reason, therefore Centralized Identity Manager can help you to create accounts with the same standards and password.
Active Directory Integrated Business Applications: Similar to applications which are not integrated with Active Directory, many other applications are Active Directory aware and can be integrated with Active Directory to use domain credentials or for the authentication purpose. In some cases, even though the application is using Active Directory credentials but Application Owners need to create local users with the information in order grant permissions on the applications. Which includes the domain name and Samaccountname, in few cases even UPN (User Principal name). so, application forwards authentication request to Active Directory to authenticate user account.
Office Automation: Services like Office Automation can be mostly automated using Centralized Identity & Access Manager, some of the tasks like User account on-boarding, Role/Department/Country Transfer and Off-Boarding process.
Business Logic Rules: There are many requirements where some of the Business logic is applied to achieve some tasks, which can be achieved. For example, if the user off-boarding process is initiated, all the permissions are revoked with the help of Centralized Identity Manager but there are third-party services/applications, where your Enterprise do not have control on system, in such cases automated emails are notified to revoke access, HRWorkways is one of the example where the enterprise outsource Payroll related workload.
Role based entitlement Rules: it is nothing more than role based access control, so if the role/department/country of the user is changed the respective changes are done automatically, for example if the city of the User is changed in HR Portal from New York to Washington DC, the user is automatically removed from New York Employees Distribution list and added to Washington DC Employees DL.
Work Order Manager: This option may not be available in all the Identity & Access Management systems but few of them has it. Basically, for the users who are separated from Enterprise, but as part of the Enterprise’s Retention policy, it is necessary to preserve user related data for 18 months, 5 years or for infinite period. It depends upon the grade, pay scale and many other factors which are defined by the Legal department of the Enterprise. So, Work Order manager helps you to create a job for the future date with the steps to be executed, like after 18 months the user account should be deleted from the respective applications, Mailbox data is either removed from hold or deleted, User files are deleted after the retention period. [It might change or may not under GDPR rule in European Union under “Right to Forgotten”].
Communication: is also possible, like when the user is on-boarded the Welcome Email notification, email from the application when access is granted in the application. So, there is a possibility which can be leveraged from the application to notify user about identity being used. [ It may require under GDPR rule in European Union].
Author: – Praakassh Ghaitadke

